Comprendre le fonctionnement du chiffrement
Vous entendez probablement beaucoup le mot cryptage, mais savez-vous vraiment ce que cela signifie? Lorsque vous magasinez en ligne, le magasin vous dit que vous ne devez pas vous inquiéter car il chiffre votre transaction. Lorsque vous envoyez un message ou envoyez un e-mail à quelqu'un, l'application indique qu'elle crypte vos messages.
Qu'est-ce que cela signifie réellement?
The term encryption refers to the encoding of any Internet message in such a way that only the intended addressee can decode it. Internet message literally means any data sent via the Internet, not just a text or email.
Encryption software transforms the data sent into cipher text. If an individual did manage to steal the data sent, they could not read it unless they had the decryption key.
Military-Grade Encryption
If you send something using a method that says it uses military-grade encryption, you will have sent it in a manner that proves nearly impossible to crack. Military-grade encryption uses 256-bit keys to create 2^256 possible combinations. No human can encrypt something using military grade encryption. Not even a supercomputer can crack an encrypted key in a reasonable time period.
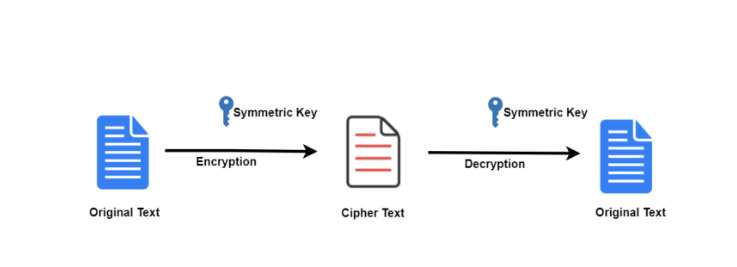
Symmetric Encryption
Symmetric encryption is when a sender and a receiver use the same private encryption key to decode and encode an encrypted message. The main drawback is that the key should be shared between the parties. Unless a secure tunnel is established, an interceptor might snatch the key and decipher the message.
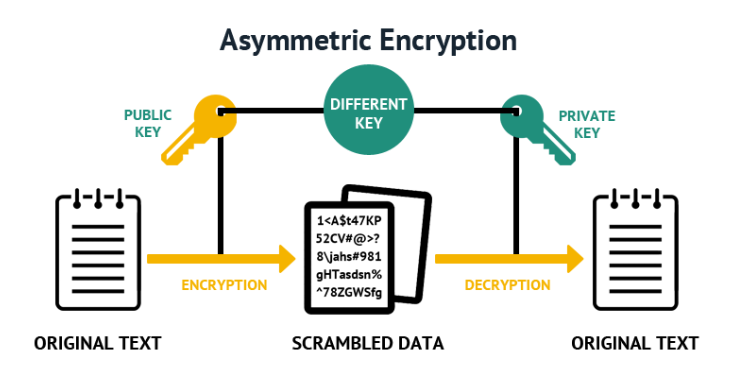
Asymmetric Encryption
Asymmetric encryption uses a two key method to for greater safety. A public key and a private key protect the message. Both sender and receiver use the shared public key, while each gets their own private key. You need both to access the message. It does leave the end-points unprotected.
Here Is an Example of How Asymmetric Encryption Works:
1) Message is encrypted using the Receiver Public Key
2) Receiver decrypts the message using his own Private Key
Authentification asymétrique:
Les deux mêmes clés peuvent effectuer l'authentification:
1) Sender signs his data with his own private key
2) Le destinataire peut authentifier que les données proviennent de l'expéditeur à l'aide de sa clé publique connue.
3) No data is encrypted
End-To-End Encryption
End-to-end encryption (E2EE) encrypts data throughout the transportation between the two end-points, including through intermediate servers. No third party, not even your Internet Service Provider (ISP) car read it. Backup or peer-to-peer (P2P) services sometimes call E2E encryption by another name – client-side encryption. Other times, it’s referred to as zero-knowledge encryption. An example of end-to-end encryption can be found on apps such as Facebook Messenger ou Telegram, cependant, aucun des services de messagerie ne l’active automatiquement.
Learn more about how encryption protects you and how it can help you protect the public safety with Solutions RadioIP. We can help you surf the Internet more safely and help first responders conduct business more privately and safely. Radio IP: we redefine secure mobility.


Sans commentaires
Désolé, le formulaire de commentaire est fermé pour le moment.